Restricting Service Account Access
It is possible to restrict access to Cronofy to a subset of users and resources within your organization. This is configured using Google’s Organizational Units.
Configuring Organizational Units #
In this example we will create an Organizational Unit, named “Resource”, as a child resource of our root domain:
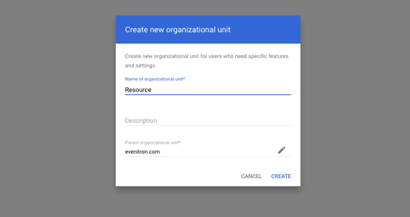
In order to authorize the application to use the Organizational Unit, a user must be created within this Organizational Unit. This user must be configured to be granted the following admin privileges:
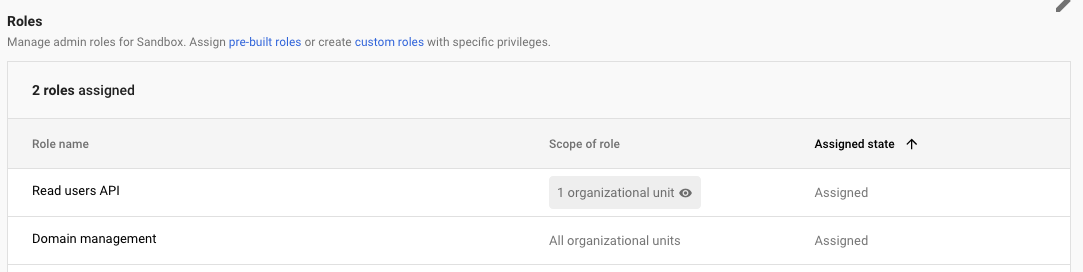
- For the Organizational Unit we created:
- Admin API > Users > Read
- For all Organizational Units:
- Admin API > Domain Management
“Users Read” is for listing users/resources (i.e. rooms) in order to add to Cronofy later on. The following scopes are included in the authorization process:
admin.directory.user.readonly
admin.directory.resource.calendar
“Domain management” is for retrieving the primary domain for the process of verifying the service account. The scope included is:
admin.directory.domain.readonly
Please note that the scope requested is “readonly”. That means Cronofy can only view and cannot make any changes.
This can be achieved by assigning each privilege via a distinct custom role:
Restricting access to the Cronofy Application #
At this stage the Cronofy application should be installed for the domain. If Cronofy has not been installed yet, please see our Enterprise Connect for Google Workspace documentation.
After installing the Cronofy Application at the root domain level, we can restrict access so only the users in our Organizational Unit have access to Cronofy. This will block access to Cronofy for all users outside of the specified Organizational Unit.
Start by going to the Cronofy Application on your Google domain.
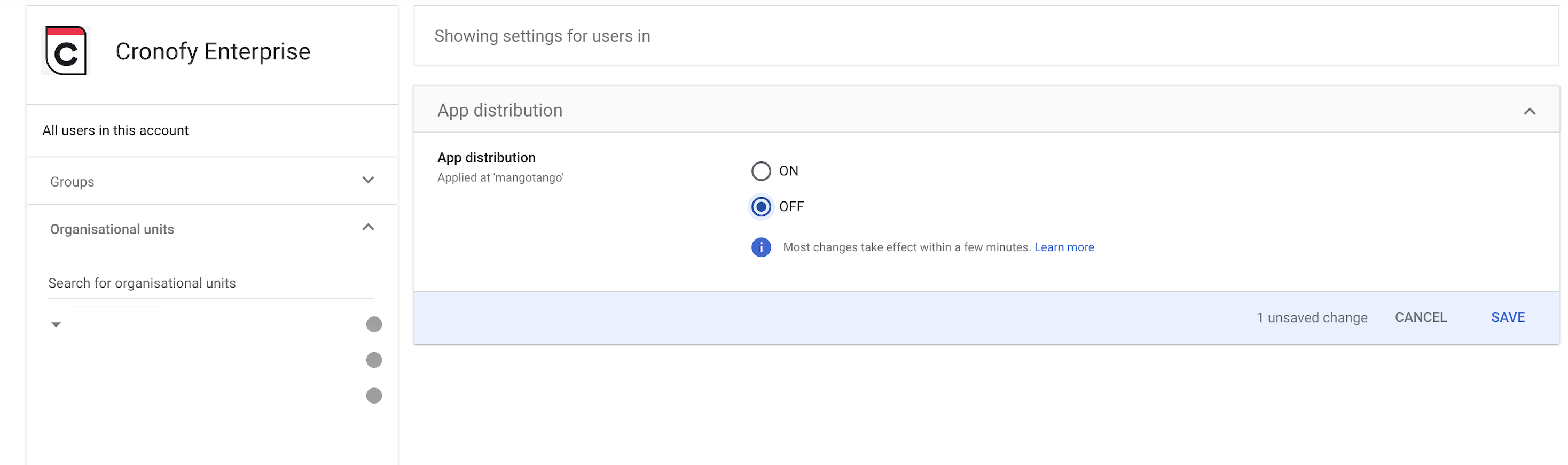
The next step is to configure overridden access for our Organizational Unit to allow access to the application. This can be done by changing the Service Status to “On”.
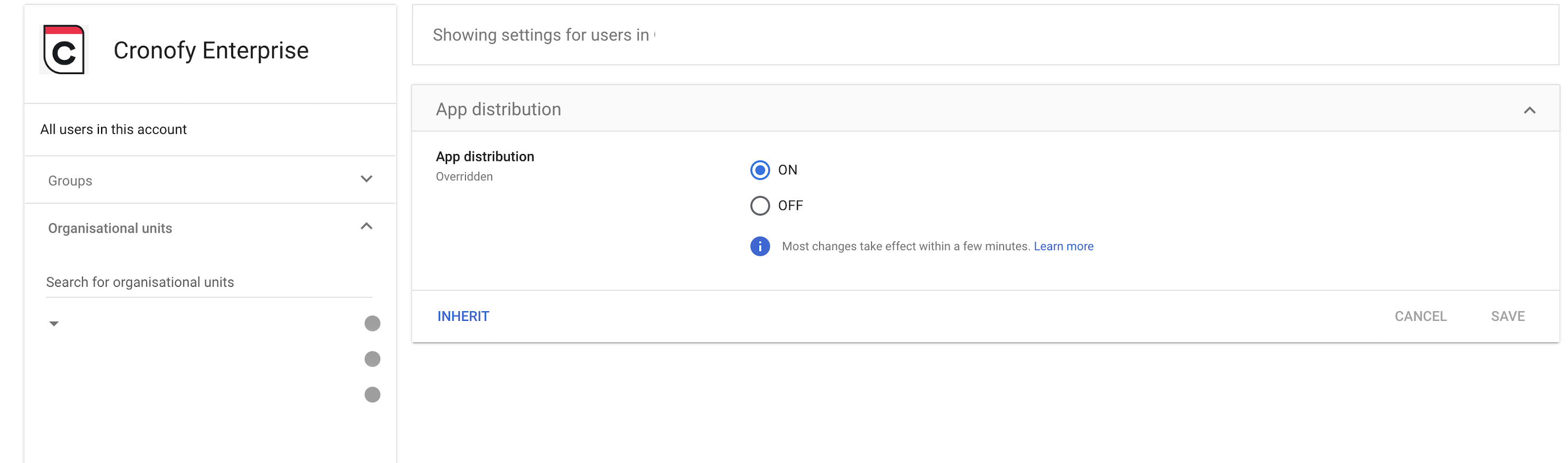
Cronofy still makes use of domain-wide delegation, but will be sandboxed within the Organizational Unit. When authorizing the Google Service Account with Cronofy, the newly created user must be used when linking.
After this process has been completed, any user accounts which should have access to Cronofy must be placed within the Organizational Unit. By default, all resources will be accessible and they can be linked.
Further reading #
For more information on Organizational Units, see Google’s documentation “Turn on or off a Google Workspace Marketplace app for users”.
For an overview on organization structures within Google Workspace, see Google’s documentation “How the organizational structure works”.
For more information about assigning an admin role, see Google’s documentation “Administrator privilege definitions”